-
The User that will be fetching on behalf of does not need to be an admin (or have admin privileges). However, an admin (or a user with
security_adminprivileges) may be required to complete some of the following steps. -
Create the user that will be used. Let’s call this user
gleansearch. -
Create a custom role. Let’s call this
CustomRole. -
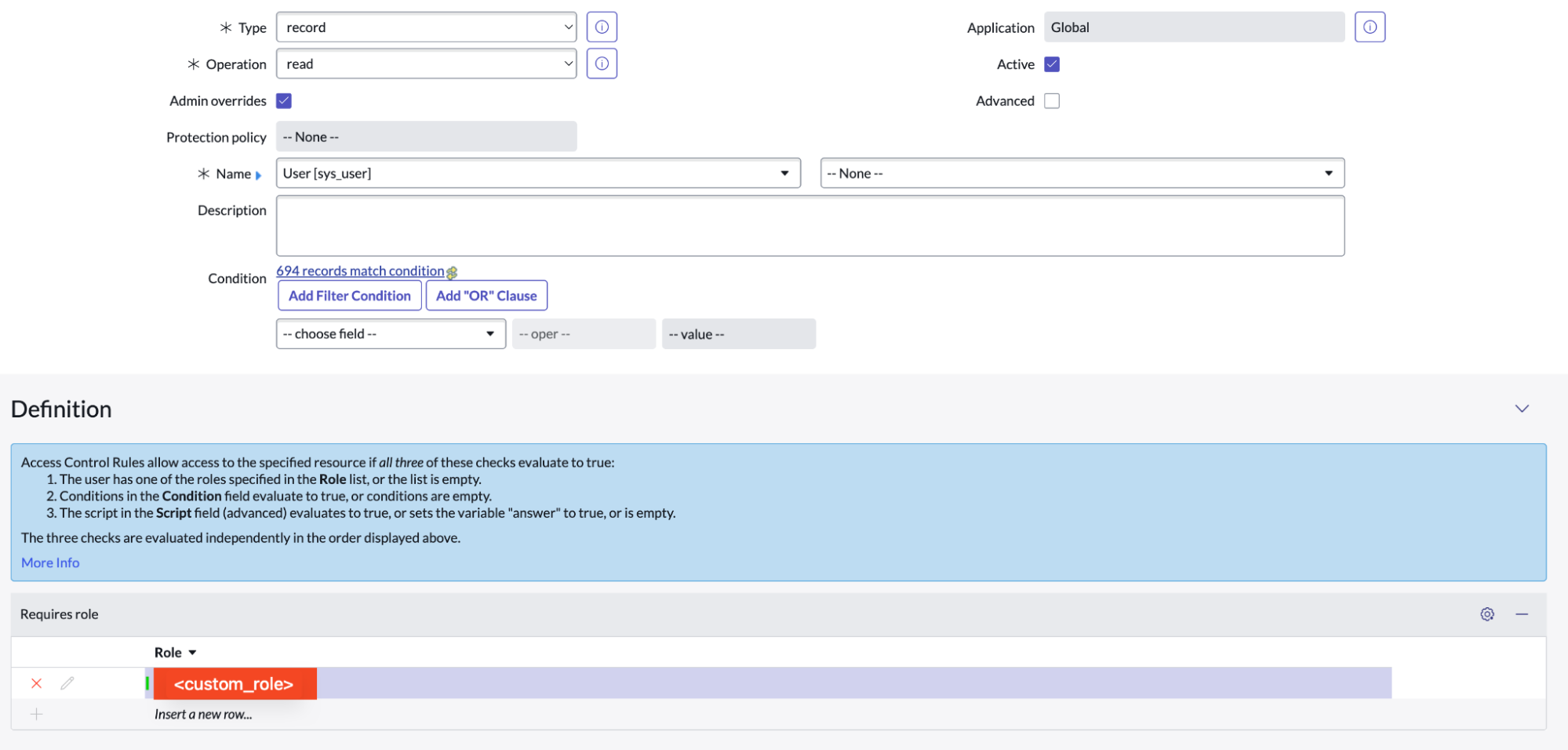
Click on the user (Organizations > Users) and then set
CustomRolefor the usergleansearchunder Roles near the bottom of the page. -
When creating the ACL Rule (System Security > Access Control (ACL)) for the Scripted REST API, then set
CustomRoleas the role for the ACL Rule. -
Set the ACL Rule that requires the
CustomRolefor both the new Scripted REST API and the/user_criteriaendpoint. -
In step 3, instead of setting roles for the user, provide read access to the necessary tables. As a security admin, you can do this by creating a new ACL Rule for each table, granting
CustomRolethe read record access. You also need to provide the read access for all fields of the table, which is done in a separate ACL Rule. Ultimately, you will create two ACL Rules for each of the following tables:sys_usersys_user_rolesys_user_has_rolesys_user_groupsys_user_grmemberuser_criteriakb_knowledgekb_knowledge_basekb_uc_can_read_mtomkb_uc_cannot_read_mtomkb_uc_can_contribute_mtomkb_uc_cannot_contribute_mtomkb_categorykb_usesc_cat_itemsc_cat_item_user_criteria_mtomsc_cat_item_user_criteria_no_mtomsc_categorysc_catalogtopicsys_audit_delete(if provided access)incident(if enabled)cmdb_ci_business_app(if enabled)dmn_demand(if enabled)pm_project(if enabled)rm_epic(if enabled)
- ACL to read the table (e.g.
sys_user) - ACL to read the properties of the table (e.g. sys_user.*)
- Add the itil (Information Technology Infrastructure Library) role to the user gleansearch. This enables the user to read tables interaction (Interactions) and sc_request (Requests)
- Follow the subsequent steps as described in the instructions and then you should be all done.